ForumIAS announcing GS Foundation Program for UPSC CSE 2025-26 from 27th May. Click Here for more information.
Source- This post on phishing is based on the article “India one of the key geographies affected by phishing attacks: Verizon” published in “The Hindu” on 1st May 2024.
Why in the News?
A report from Verizon Business has emphasized the rising incidence of phishing in India. Cybercriminals are resorting to new and sophisticated methods to deceive unsuspecting users into opening malicious emails or clicking on harmful links.
As a result, there is an increased risk of users experiencing financial losses and the compromise of their personal data.
Highlights of the study:
a) The report highlighted that there has been improvement in reporting practices of such incidents of phishing in India. However only 20% of users now identify and report phishing during simulation tests.
b) Another Report of the company reveals that espionage attacks dominate the cyber security landscape in the Asia-Pacific region, including India.
c) In the Asia-Pacific region, 25% of cyberattacks stem from espionage, a stark contrast to the 6% and % in Europe and North America, respectively. The Asia-Pacific region saw a 180% growth in vulnerability exploitation.
d) System intrusion, social engineering, and basic web application attacks represent 95% of breaches in Asian Pacific region.
e) The study also found that the most common types of data compromised are credentials (69%), internal (37%), and secrets (24%).
About Phishing
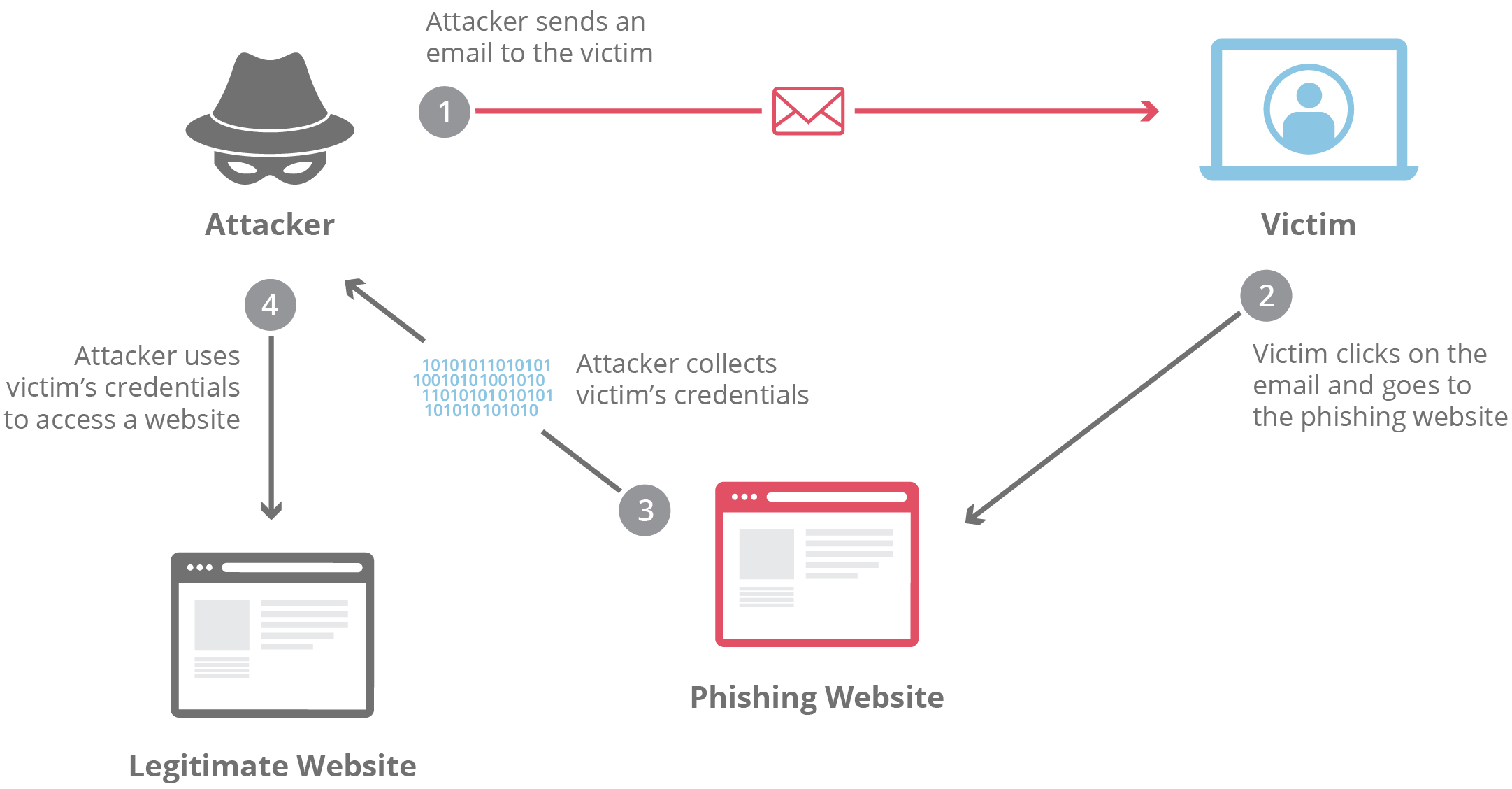
1. About Phishing: It refers to an attempt to steal sensitive information in the form of usernames, passwords, credit card numbers, bank account information or other important data to utilize or sell the stolen information.
2. How Phishing is done:
a) In a phishing attack, the sender pretends to someone trustworthy to the recipient, such as a family member, the CEO of their company, or a well-known figure offering giveaways.
b) The message prompts immediate action, often with a sense of urgency and directing the recipient to a fake website resembling a legitimate one.
c) They are asked to input their login credentials which are then stolen by the attacker for identity theft, financial fraud, or selling personal information. The phishing email’s destination URL closely resembles the legitimate one.
UPSC Syllabus: Science and technology




